Configuring Duo Single Sign-On (SAML) for FortiGate
With the announcement of iFrame support ending in Duo, many organizations are switching over to the new “Fortinet FortiGate – Single Sign-On” option. Additionally, for organizations using an LDAP integration, there is no ability to select where to send the Duo Push notification and it will default to the first option. Setting up the “Fortinet FortiGate – Single Sign-On” integration involves potentially making a few changes, depending on how your SSL-VPN instance is setup. Earlier builds of 7.2 and 7.4 require additional FortiClient parameters for SSL-VPN to authenticate correctly.
It is important to note that when using Duo with FortiGate VPN all users must be setup in Active Directory and that they do not exist as local SSL-VPN users on the FortiGate. If a username matches an Active Directory user, that account can still be signed into locally on the FortiGate bypassing Duo.
Duo Configuration
In the Duo Admin Center, go to Applications > Protect an Application and search for “Fortinet FortiGate” then select Protect. Scroll down until you see the Group Membership Attribute and enter a Fortinet group name that matches a group on the FortiGate, then select a Duo group (or multiple).
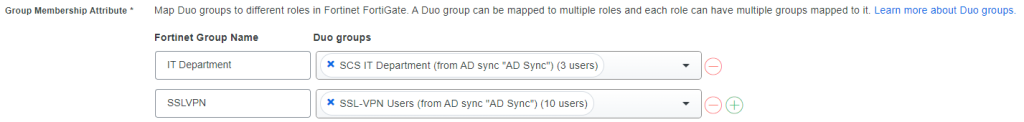
Scroll back up to the Metadata section and download the idp-cert.
FortiGate Configuration
Login to your FortiGate firewall and go to System > Certificates. Select “Create/Import” then Remote Certificate. On the Upload Remote Certificate screen, select the idp-cert you downloaded from Duo earlier and select OK.
Next, go to User & Authentication > Single Sign-On select “Create New” in the upper left-hand corner. Set a name that you will remember later, and enter the Public WAN IP Address under the Address Section. This IP Address must include the port used for the SSL-VPN Portal.

We will want to copy the Entity ID and Assertion consumer service URL over to the entity-id and single-sign-on-url on Duo’s end before proceeding. Once entered on Duo’s side, select the Save button.
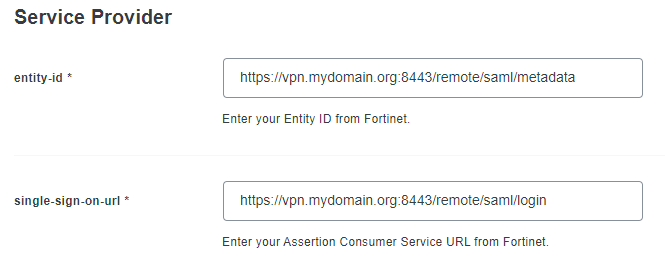
Return to the FortiGate webpage and select Next. Enter the following information on this page:
Type: Custom
Entity ID: <idp-entity-id from Duo>
Assertion consumer service URL: <idp-single-sign-on-url from Duo>
Single logout service URL: <idp-single-logout-url from Duo>
Certificate: <Certificate uploaded earlier> Name should begin with REMOTE_Cert_X with X representing a number.
Attribute used to identify users: Username
Attribute used to identify groups: Group

The last step is to link the permitted groups from Duo to the newly created SSO profile so that users can start logging in. To do this, go to User & Authentication > User Groups on the FortiGate. Under the group(s) you wish to use Duo with, add the newly created SSO group and then press OK.

Duo should now be configured and secured so that users cannot bypass Duo authentication by logging in with a local user.
One other important thing to note with this configuration, based on version 7.2.8 is the inability to configure automatic reconnection when using SSL-VPN. I have been unsuccessful in making this work correctly where Duo will not prompt if reconnected to within 240 seconds, especially if the network is changed.